As we have all heard over and over again, these are unprecedented times. Organizations are scrambling to adapt to the situation and to setting efficient working from home policies and procedures. Many organizations are actually being forced to go through a long-overdue digital transformation process to be able to survive in these conditions. Leveraging SaaS platforms like Slack, Jira, Zoom, Microsoft Teams, and WebEx, teams are finding new ways to collaborate and manage their daily work tasks. These platforms have seen exponential growth in daily active users, and this has not only tested the resilience of their team and backend software development, but also the stability and scalability of cloud infrastructure providers that support them like AWS, GCP, and Azure.
Of course, this sudden growth of users comes with its own set of problems, and in the case of Zoom, it was a cybersecurity and privacy problem. You can read about all the backlash the company has faced in the news, albeit a bit harsh in my opinion considering the pressure they were put under in such a short period of time. Many of the Zoom client vulnerabilities and concerns that have been made public have already been patched by Zoom.
I will focus in this commentary on basic measures to improve the cybersecurity and privacy of the Zoom service, especially for the organizations that hurried into starting to use Zoom without really looking at settings and configurations.
Meeting Room IDs
Everyone should be aware that there are two types of meeting room IDs that every user has access to with each having a different use case.
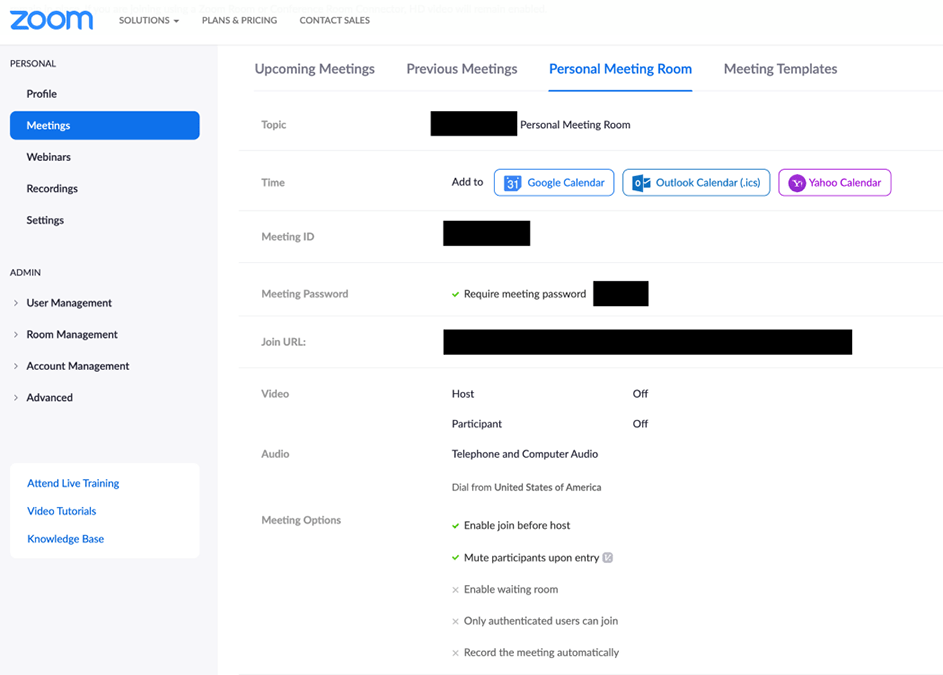
Personal Meeting Room ID
Every user has a personal ID that does not change and is used for “instant meetings” in what zoom calls a “Personal Meeting Room”. Some settings for this type of meeting room are set from a different page than the general settings applied to “scheduled meetings”. You can navigate to this specific settings page to follow my below recommendations that will make things more secure.
- “Meeting Password and Join URL”: Now this is a strange way of implementing things by Zoom, but it seems for the sake of convenience they have decided to embed the password into the link which kind of defeats the purpose of the password. Once the URL link is shared, the invitee does not require the password to join. (There does not seem to be a way to remove the password from the URL).
- “Enable waiting room”: The best way to mitigate the risk here is to enable this option, which gives you granular control on who is allowed into the meeting once it starts.
- “Only authenticated users can join”: Enable this option to only allow signed-in Zoom users to join (you can also limit to certain domains).
Scheduled Meeting Room ID
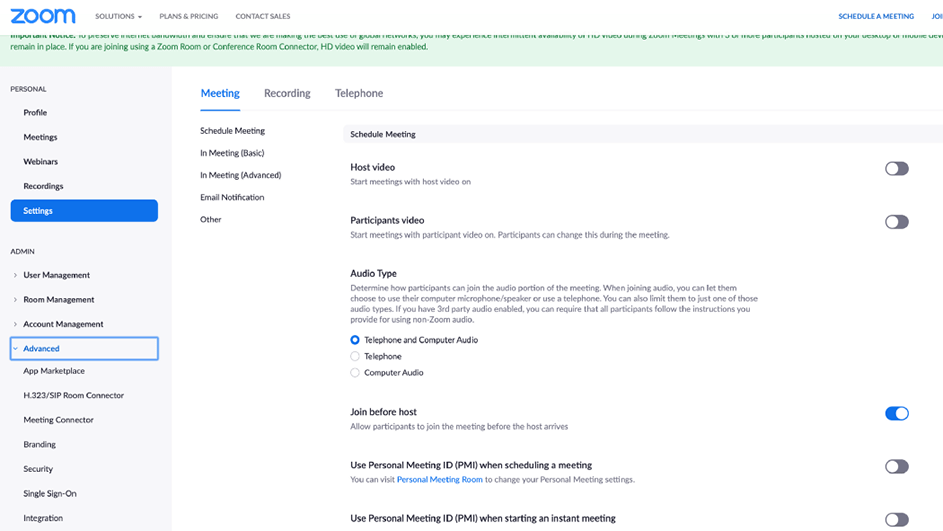
These IDs are generated automatically when you are scheduling a meeting and inviting other users via email or sharing the meeting URL link. As I mentioned before, the general settings apply to these types of meetings and are set from another page than the personal meeting room ID settings above. You can again navigate to this settings page to follow my below recommendations that will make things more secure.
- “Use Personal Meeting ID (PMI) when scheduling a meeting”: Make sure this is turned off to force Zoom to create a new meeting ID and URL for every meeting.
- “Only authenticated users can join meetings”: Enable this option to only allow signed-in Zoom users to join (you can also limit to certain domains).
- “Require a password when scheduling new meetings”: This should be enabled.
- “Embed password in meeting link for one-click join”: If you are going to enable passwords, then it only makes sense if you disable this option. Every organization needs to decide on what is best for them and how to balance security and convenience.
- “File transfer”: This setting should be disabled, and force users to use other means like email to send files because that will include a certain level of security.
- “Screen sharing”: Restrict to the default option that only allows the host to share his screen. A host can still grant screen-sharing privileges to specific users during a meeting.
- “Disable desktop/screen share for users”: I recommend this is enabled, as from experience I have seen many people unknowingly share their desktop and expose sensitive information by allowing invitees to view their private files, folders, and open windows.
- “Far end camera control”: This option should be disabled for obvious reasons.
- “Waiting room”: Attendees cannot join a meeting until a host admits them individually from the waiting room. The best way to eliminate the risk of unwanted attendees is to enable this option, which gives you granular control on who is allowed into the meeting once it starts. Might not be a suitable option for hosts who hold large meetings.
- “Blur snapshot on iOS task switcher”: Should be enabled to reduce the possibility of sensitive information being exposed.
Casual Users
For more casual users or classrooms there is one very important action that can be done after a Zoom call starts and all invitees have joined, which is to “Lock” the call. This will prevent anyone else from joining and can be done by clicking the button that says “Lock Meeting” in the Participants pop-up.
General User Profile Security Settings
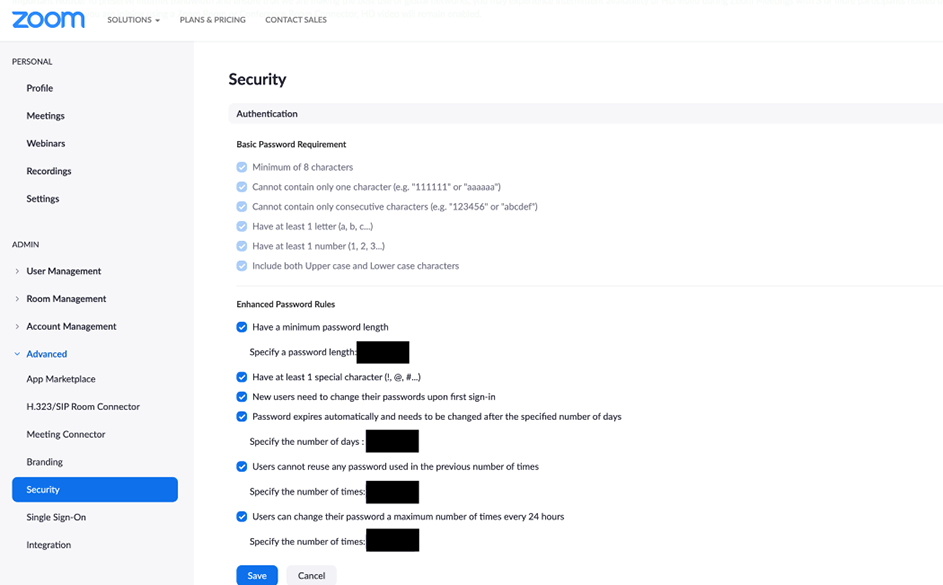
General user settings that mitigate the risk of users' accounts getting compromised are also very important. These are settings that can only be enforced by the Admin of the Zoom account. You can again navigate to this settings page to follow my below recommendations that will make things more secure.
- “Basic Password Requirement” and “Enhanced Password Rules”: All options under this should be enabled to force users to use complex passwords that are changed regularly.
- “Users need to sign in again after a period of inactivity”: Admins need to make sure to input a reasonable inactivity period based on the security profile of their organization.
- “Sign in with Two-Factor Authentication”: This should be enabled and would eliminate most of the risk related to breached credentials.
- “Allow users to sign in with Facebook and Allow users to sign in with Google”: Should be disabled.
IOS and Android Apps
Users should also take certain measures on the mobile apps by taking advantage of the security measures that iOS and Android OS have. You can update your privacy settings for the Zoom app to restrict its access to your location, contacts, calendars, microphone, camera, assistant, notifications, and cellular data.
Other Concerns
There are some major concerns about Zoom that no setting can really fix, those would be something every organization needs to evaluate based on their threat model to see if they are willing to take those risks with their data. Some of these concerns highlighted by Citizen Lab are related to their end-to-end encryption methodology and routing of traffic through servers in China. Zoom did respond to the Citizen Labs findings in a blog post by their CEO.
Author Info


