Long gone are the days when a set of logical cybersecurity safeguards would be considered sufficient to protect an organization from threats of ransomware. With the growing scale and sophistication of this emerging class of cyberattacks, if you think your organization has all what it takes to protect itself against a ransomware attack, I urge you to reconsider. Ransomware criminals have been employing multi-pronged attacks that involve not just encrypting files and locking operating systems, but also exfiltrating and destroying data and executing denial of service (DoS) attacks on the underlying infrastructure. No organization of any size is immune to this class of cyberattacks.
The Lockheed Martin Cyber Kill Chain® offers cyber defenders a model they can leverage to understand an organization’s IT environment, the weaknesses that may allow an attacker to compromise its systems, and the mitigations that should be put in place. This framework inspects a ransomware attack lifecycle and breaks it down into seven key steps. Understanding each step in the kill chain helps inform what protection mechanisms should be applied. Beyond just the technology, a deep dive into process and people-oriented cybersecurity protection is key to thwarting ransomware attacks and preventing their advancement to the next steps in the chain. In what follows, we break down these protections based on the Kill Chain® framework.
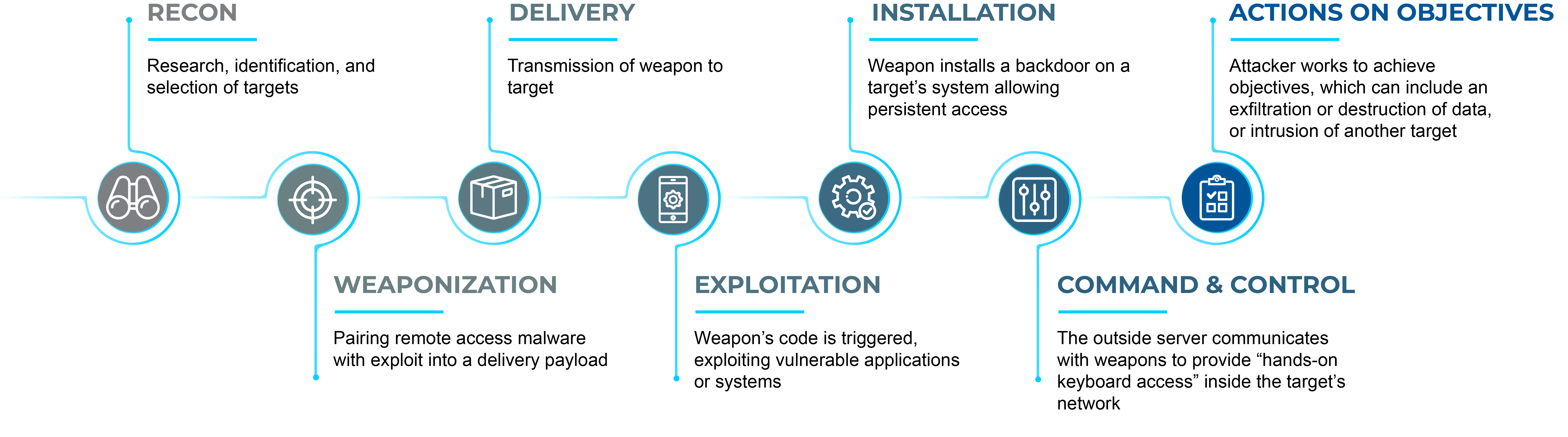
Almost all ransomware attacks begin with Reconnaissance. Attackers investigate their target using available sources of information with activities like network scans, browsing websites for directory information, looking for email addresses of executives, etc… with the goal of learning as much as possible about the intended target to find potential avenues of attack. Once a target is identified, recon about what avenues of compromise can be exploited are also inspected. This could take the form of vulnerabilities or misconfigurations in the target system. To prevent your environment from giving away information about applications, data, or weaknesses in the underlying IT infrastructure, it is recommended that organizations take proactive steps to assess the security architecture of their infrastructure and its design and that the implemented logical controls meet industry security recommendations. Setting up effective security monitoring and analysis for incoming web traffic ensures that only legitimate visitors are allowed on a web application and prevents malicious web crawling tools from achieving recon goals. Although security monitoring and analysis is mainly a detective process, a SOAR capability provides protection mechanisms through threat data collection and automated response to security events.
Weaponization occurs once a vulnerable pathway is found into the target organization and an exploit is crafted to suit the vulnerability detected. Secure coding principles should be an integral aspect of software development lifecycle. In addition, security reviews and tests (ex. code reviews, vulnerability scans, and penetration testing) should be carried out periodically on existing applications to identify weaknesses, and a shift left approach to security requirements should be implemented as part of any new system acquisition and software development project management activities. A robust vulnerability and patch management program will ensure that weapons targeting identified vulnerabilities will fail to achieve their objective. A cybersecurity maturity assessment can identify gaps in the implementation of these protection mechanisms and provide recommendations to achieve target state protection requirements.
Delivery involves transmitting the weapon to the target system. This can occur in any number of ways, including avenues as simple as sending a phishing email to a user, or a more complicated transmission medium like an exploited service running on a system that allows for the remote execution of malware. The best line of protection against this is strong user awareness. Organizations that ensure users are periodically trained on cybersecurity aspects, run campaigns to raise awareness, and execute phishing simulations are best equipped to evade threats of ransomware. Security reviews and testing can reveal security misconfigurations that can be then corrected by a security engineering team.
Exploitation is the execution of the weapon delivered. It takes some form of control over the exploited system. The traditional goal of most attackers is to be able to obtain escalated access to an exploited system and have complete control, though lesser forms of access can still be useful for activities like data exfiltration. Access control is paramount at this step. A thorough assessment of existing access control procedures will yield a set of recommendations that help achieve strong protection against this step of the kill chain.
Installation involves the attacker finding a way to maintain persistent access to the compromised system, which means that if a system admin identifies and removes the malware installed, the goal is to still have a covert way to access the compromised system. Command and Control, or C2, is the step in the kill chain where the compromised system establishes a connection to a command-and-control environment. This remote connection is how the attacker interacts with the compromised system or the location where the data stolen is sent to. Ensuring that security logs are protected, monitored, and analysed for suspicious activities, connections, and abnormal behaviour will play a big role in detecting and preventing the success of the actions taken in these two stages of the attack.
Actions on Objectives is the final step in the chain where the intended goal of the whole attack is achieved and where all the previous steps culminate. This is where data exfiltration or data destruction usually occur. Here, a successful data classification and data loss prevention program will protect the organization’s crown jewels from falling in the wrong hands. This would typically include the establishment of a data classification scheme, classification of structured and unstructured data, enforcing the use of asset labelling, and implementation of a data loss prevention program. Additionally, data minimization principles that require the collection and retention of only the data necessary for accomplishing business missions would greatly prevent the leakage of information that might otherwise be unnecessarily stored without an explicit business need or defined lifetime.
Get in touch with us at Axon Technologies to inform you about how our team of seasoned GRC consultants, security architects and engineers, and cyber fusion centre specialists can be your cybersecurity partners, helping you step up your protections against ransomware because, frankly speaking, no organization would want to be the next ransomware statistic!

